Malware analysis https://mail-bigfile.hiworks.biz/service/download/472529a3ba6f34c04b00186f0faecc84af0c95afe0a9ff72689aec5c13b4eaea Malicious activity | ANY.RUN - Malware Sandbox Online

PHP : Warning: file_get_contents(): https:// wrapper is disabled in the server configuration by all - YouTube
Malware analysis https://rvklk.loveiswaiting.net/c/9c0ffb42cc386357?s1\=30638&s2\=982137&s3\=45&s5\=260541&click_id\=NTkgWVbLRWSMNoVu3j7xBAAAUSkAAAAGAAAALQAAAAAAA_m9ABye1wAAAAD-0U2w&j1\=1&j7\=1 Malicious activity | ANY.RUN - Malware Sandbox Online

Warning: file_get_contents(): http:// wrapper is disabled in the server configuration by allow_url_fopen=0 - General topics - PrestaShop Forums
SSLError HTTPSConnectionPool(host='www.coursera.org', port=443): Max retries exceeded with url: /api/login/v3 · Issue #661 · coursera-dl/coursera-dl · GitHub
Malware analysis https://drive.google.com/file/d/1L-AGdCCiOgjlzDQfgR1Vn_ytu9CebZiJ/view?usp=sharing No threats detected | ANY.RUN - Malware Sandbox Online

Outlook phishlet missing correct domain? (goproxy related "Cannot write TLS response body from mitm'd client") · Issue #248 · kgretzky/evilginx2 · GitHub
Malware analysis https://rvklk.loveiswaiting.net/c/9c0ffb42cc386357?s1\=30638&s2\=982137&s3\=45&s5\=260541&click_id\=NTkgWVbLRWSMNoVu3j7xBAAAUSkAAAAGAAAALQAAAAAAA_m9ABye1wAAAAD-0U2w&j1\=1&j7\=1 Malicious activity | ANY.RUN - Malware Sandbox Online

Outlook phishlet missing correct domain? (goproxy related "Cannot write TLS response body from mitm'd client") · Issue #248 · kgretzky/evilginx2 · GitHub
Malware analysis http://www.mediafire.com/file/cpc62qc386garyx/WA.rar Malicious activity | ANY.RUN - Malware Sandbox Online
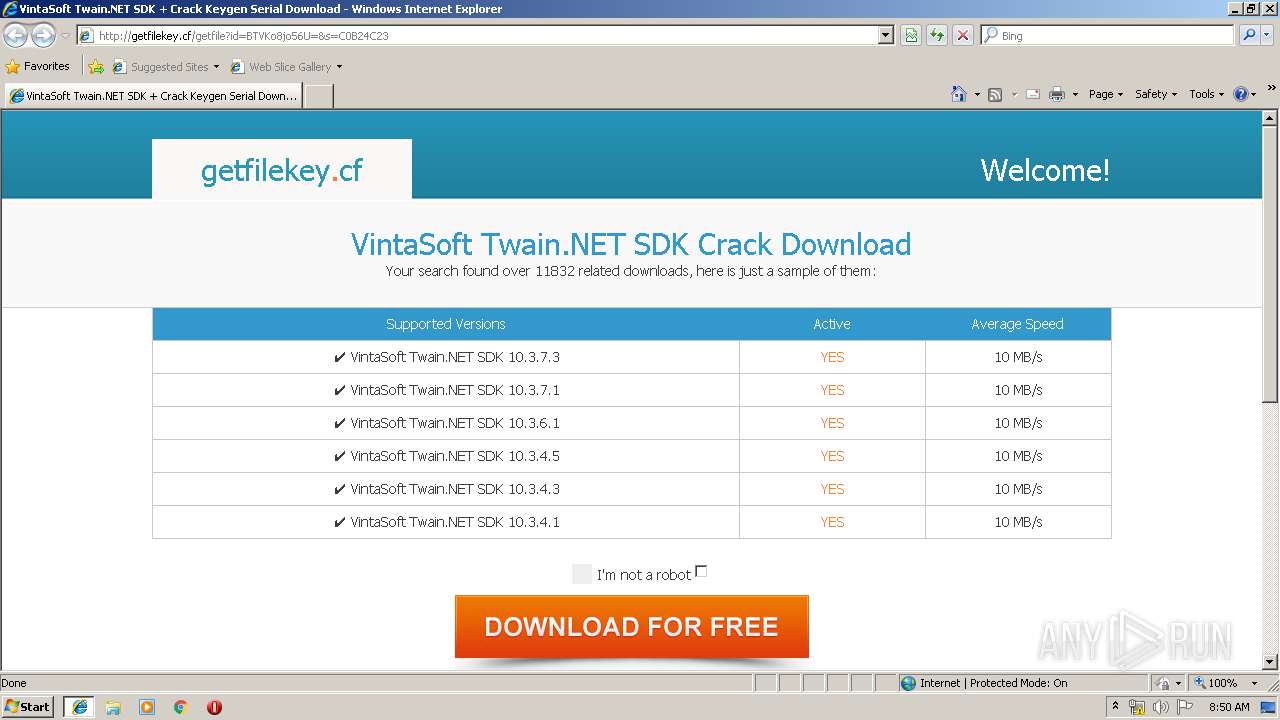
Malware analysis http://getfilekey.cf/getfile?id=BTVKo8jo56U=&s=C0B24C23 Suspicious activity | ANY.RUN - Malware Sandbox Online
![2018.UnregisteredHyperCam2.FullAlbum.XviD.KfaD.320kbps[CDRip] (cover image) : Unregistered HyperCam 2 : Free Download, Borrow, and Streaming : Internet Archive 2018.UnregisteredHyperCam2.FullAlbum.XviD.KfaD.320kbps[CDRip] (cover image) : Unregistered HyperCam 2 : Free Download, Borrow, and Streaming : Internet Archive](https://archive.org/download/2018.unregisteredhypercam2.fullalbum.xvid.kfad.320kbpscdrip-cover-image/GilvaSunner%20-%202018.UnregisteredHyperCam2.FullAlbum.XviD.KfaD.320kbps-CDRip-%20-%20hypercam%20cover.jpg)
2018.UnregisteredHyperCam2.FullAlbum.XviD.KfaD.320kbps[CDRip] (cover image) : Unregistered HyperCam 2 : Free Download, Borrow, and Streaming : Internet Archive
Malware analysis 561cb93118fef1966a3233ae7ffd31017823dd5aaad5dc1b2542e717055c197a.zip Malicious activity | ANY.RUN - Malware Sandbox Online
Malware analysis https://www.google.com/url ?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwigytX02JKDAxUGkIkEHdKAD4o4HhAWegQIDRAB&url= https%3A%2F%2Foceansofgamess.com%2Fminecraft-free-download%2F&usg=AOvVaw3Wi-Fy5A6ztzT4haXP-h0S&opi ...